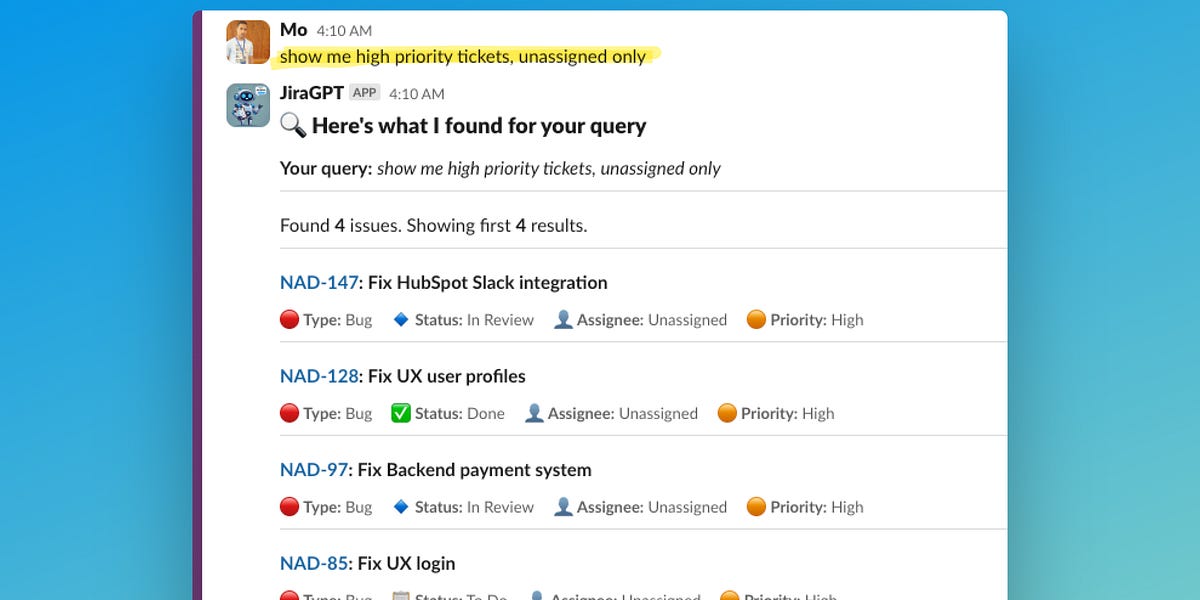
Okta AD/LDAP Delegated Authentication - Username Above 52 Characters Security Advisory
On October 30, 2024, a vulnerability was internally identified in generating the cache key for AD/LDAP DelAuth. The Bcrypt algorithm was used to generate the cache key where we hash a combined string of userId + username + password. During specific conditions, this could allow users to authenticate by only providing the username with the stored cache key of a previous successful authentication.
Note: A precondition for this vulnerability is that the username must be or exceed 52 characters any time a cache key is generated for the user.
The vulnerability can be exploited if the agent is down and cannot be reached OR there is high traffic. This will result in the DelAuth hitting the cache first.
Customers meeting the preconditions should investigate their org system log for this issue between the period of July 23rd, 2024 to October 30th, 2024.