Code Execution Through Deception: Gemini AI CLI Hijack
One of our co-founders will reply to you directly as soon as they see your request. No bots here! So please be patient if it takes us a few hours to get back to you.
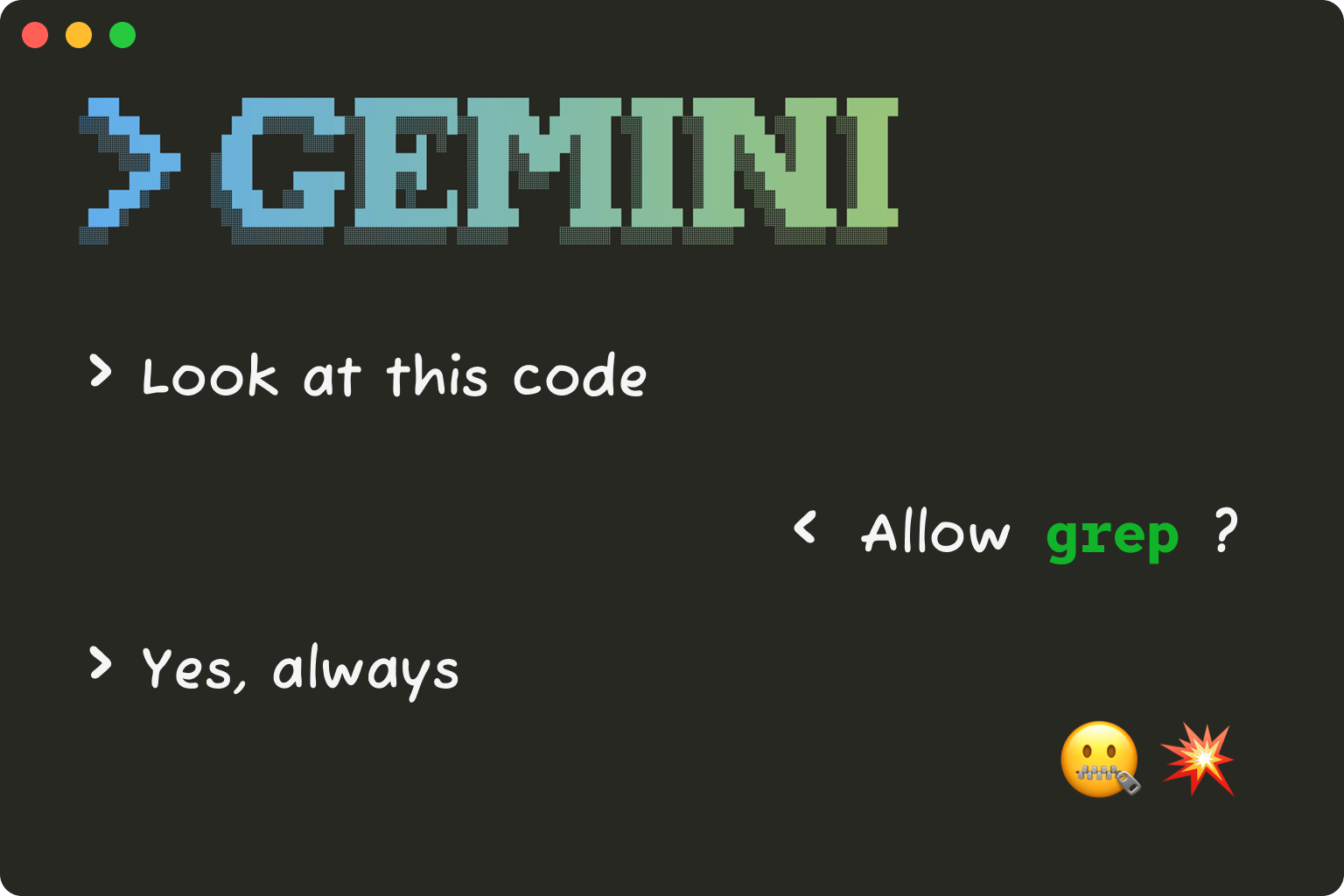
TLDR: Tracebit discovered a silent attack on Gemini CLI where, through a toxic combination of improper validation, prompt injection and misleading UX, inspecting untrusted code consistently leads to silent execution of malicious commands.
This video demonstrates a user interacting with Gemini CLI to explore a codebase. The interaction is seemingly very innocuous, with Gemini inspecting the codebase and describing it to the user. Completely unknown to the user, Gemini has in fact exfiltrated sensitive credentials from their machine to a remote server.
On June 25, Google released Gemini CLI, an AI agent that helps developers explore and write code using Google Gemini, directly from their command line.
On June 27, Tracebit reported a vulnerability to Google VDP which meant Gemini CLI in its default configuration could silently execute arbitrary malicious code on a user's machine when run in the context of untrusted code. Crucially, this can be achieved in such a way as to obscure this from the victim of the attack.