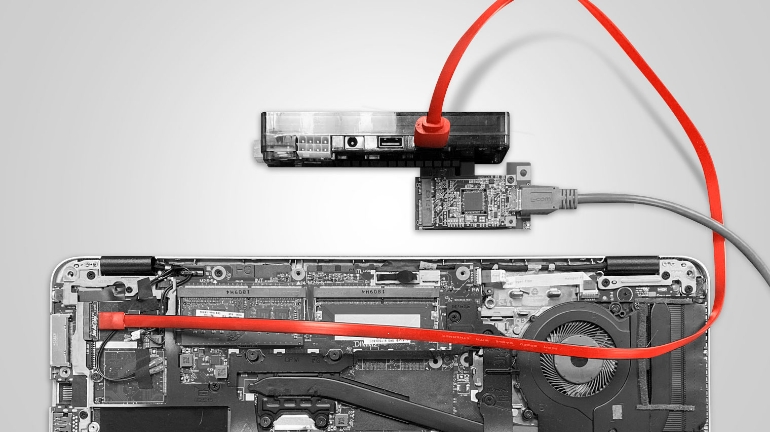
Direct Memory Access Attacks - A Walk Down Memory Lane
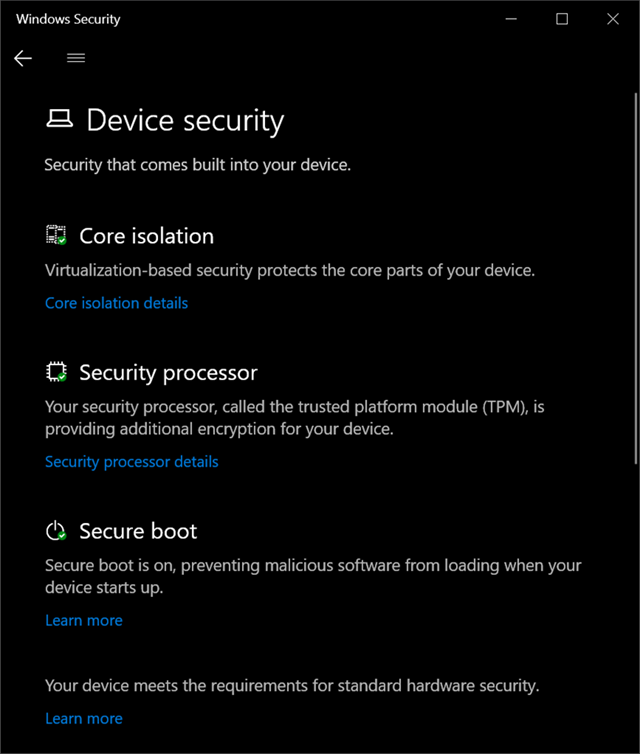
Eclypsium’s latest research shows that enterprise laptops, servers, and cloud environments continue to be vulnerable to powerful Direct Memory Access (DMA) attacks, even in the presence of protections such as UEFI Secure Boot, Intel Boot Guard, HP Sure Start, and Microsoft Virtualization-Based Security.
DMA attacks are a particularly powerful class of attacks for any adversary who has compromised firmware locally or remotely on peripheral hardware such as network cards, or who has physical access to a system. As the name suggests, DMA attacks enable a potential attacker to read and write memory off a victim system directly, bypassing the main CPU and OS. By overwriting memory, attackers can gain control over kernel execution to perform virtually any manner of malicious activity. We collectively refer to these as Memory Lane attacks.
While we will look at a few specific examples here, it is important to note this is an industry-wide issue. Previously, successful DMA attacks have been demonstrated against Intel NUC and Lenovo laptops, and these vulnerabilities apply equally to servers as well as laptops. While device vendors, chip vendors, and operating system vendors have all developed new controls to defend against these threats, our research shows that many devices with built-in hardware protections continue to be vulnerable.