![Authentication bypass in Node.js websocket module An Authentication Bypass Using an Alternate Path or Channel vulnerability [CWE-288] affecting FortiOS and FortiProxy may allow a remote attacker to g](https://filestore.fortinet.com/fortiguard/static/images/fortiguard-logo-dark-theme.svg?v=33340)
Authentication bypass in Node.js websocket module
An Authentication Bypass Using an Alternate Path or Channel vulnerability [CWE-288] affecting FortiOS and FortiProxy may allow a remote attacker to gain super-admin privileges via crafted requests to Node.js websocket module.
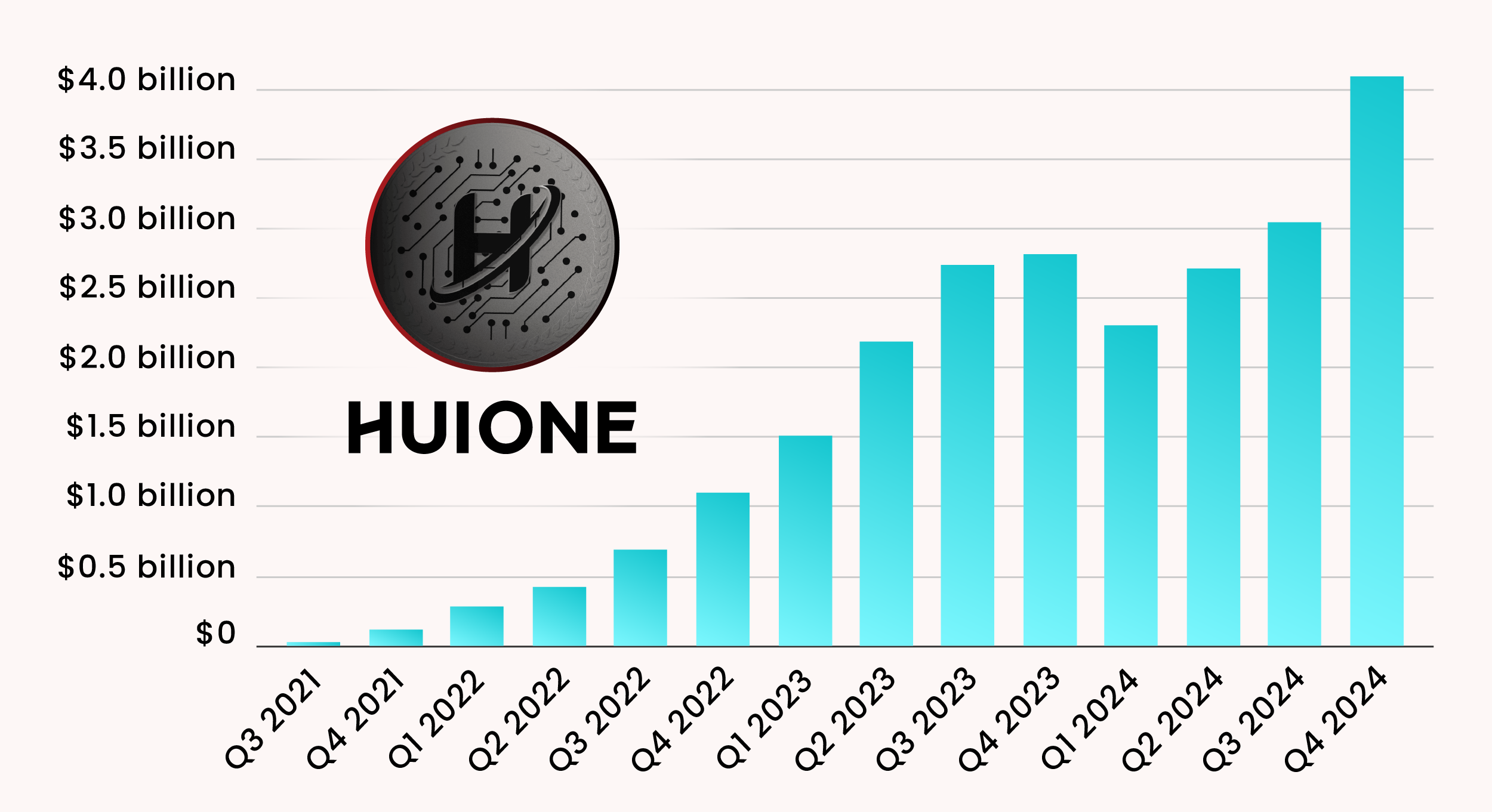
Following login activity log with random scrip and dstip: type="event" subtype="system" level="information" vd="root" logdesc="Admin login successful" sn="1733486785" user="admin" ui="jsconsole" method="jsconsole" srcip=1.1.1.1 dstip=1.1.1.1 action="login" status="success" reason="none" profile="super_admin" msg="Administrator admin logged in successfully from jsconsole"
Following admin creation log with seemingly randomly generated user name and source IP: type="event" subtype="system" level="information" vd="root" logdesc="Object attribute configured" user="admin" ui="jsconsole(127.0.0.1)" action="Add" cfgtid=1411317760 cfgpath="system.admin" cfgobj="vOcep" cfgattr="password[*]accprofile[super_admin]vdom[root]" msg="Add system.admin vOcep"
Please note that the above IP parameters are under attacker control and therefore can be any other IP address. Please note as well that sn and cfgtid are not relevant to the attack.
Leave a Comment
Related Posts






/cdn.vox-cdn.com/uploads/chorus_asset/file/25831586/STKB310_REDNOTE_XIAOHONGSHU_B.jpg)