Performing Due Diligence on Authentication Vendors
Within today’s software development ecosystem, third-party vendors are a common part of system architecture. Specifically, Authentication-as-a-Service (AaaS) is growing fast. Their out-of-the-box capabilities enable engineering teams to focus on building features valuable to business rather than spending time and resources on reinventing the wheel of securing application access.
But outsourcing isn’t as simple as it sounds. Vendor management is time-consuming and can introduce significant risks to the business if due diligence isn’t observed.
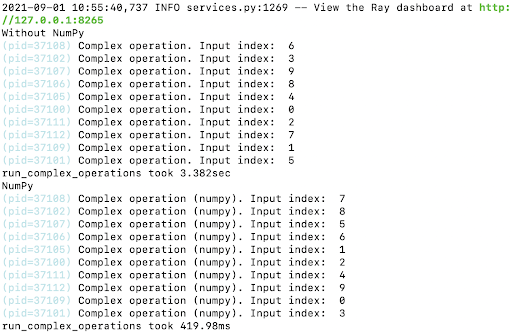
For example, the 2017 Equifax data breach consumed many organizations, including mine where I was on the information security (Infosec) team. The breach exposed the personal data of hundreds of millions of people: social security numbers, names, addresses, and more. Thankfully, our organization had the right policies in place to safeguard the personal data and no data was compromised.
We had communicated to our clients right away about the breach and ensured all servers were being patched up in case there was a leak. Our AppSec team rolled out a patch over the weekend to all of our internal servers including the ones where we hosted our third-party vendors. The team deliberately worked with our clients ensuring them the steps taken to protect them and their data. We had mitigated a huge security event. We consistently maintained information on internal servers which also listed all on-premise servers that hosted third-party vendors.





/cdn.vox-cdn.com/uploads/chorus_asset/file/24000090/acastro_STK075_02.jpg)