Gaining Access To GCP Of Google Stadia — 500$ Bounty
So far, I have been only a consumer of bug bounty write-ups. I hope I can give something back to the community by writing about my adventure!
At that time, I have learned the approach of machine- based authentication in the cloud. In particular, reading disclosed HackerOne server-side request forgery and similar vulnerability reports with the technique of gaining access to the cloud provider by connecting to the internal metadata endpoint, retrieving a service account token, and using the exfiltrated service account / token to authenticate from outside, was the key to my success. This lead me to the idea that instead of searching for SSRF (or related) vulnerabilities in a single target, I should try my luck in the big wide world of OSINT.
As far as I can remember, Github was not scanning for exposed tokens at that time. Encountering exposed credentials was painless.
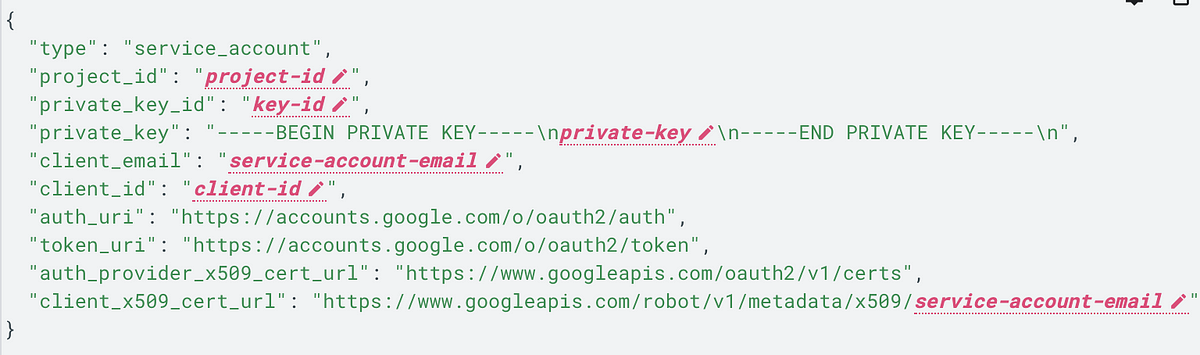
The first step is, of course, to find a way to find these services accounts. My approach is to find a unique string in the target to narrow down the search results. For example, long-term AWS IAM access key ids begin with AKIA and temporary credentials with ASIA . Google service accounts were unknown to me, I needed to lookup the structure and identify potential needles.







.png)