Safetybits | Automating Vulnerability Detection for Your Assets
Discover how to automate vulnerability detection of your assets, so you can shift left security and protect your infrastructure before a vulnerability becomes a security incident.
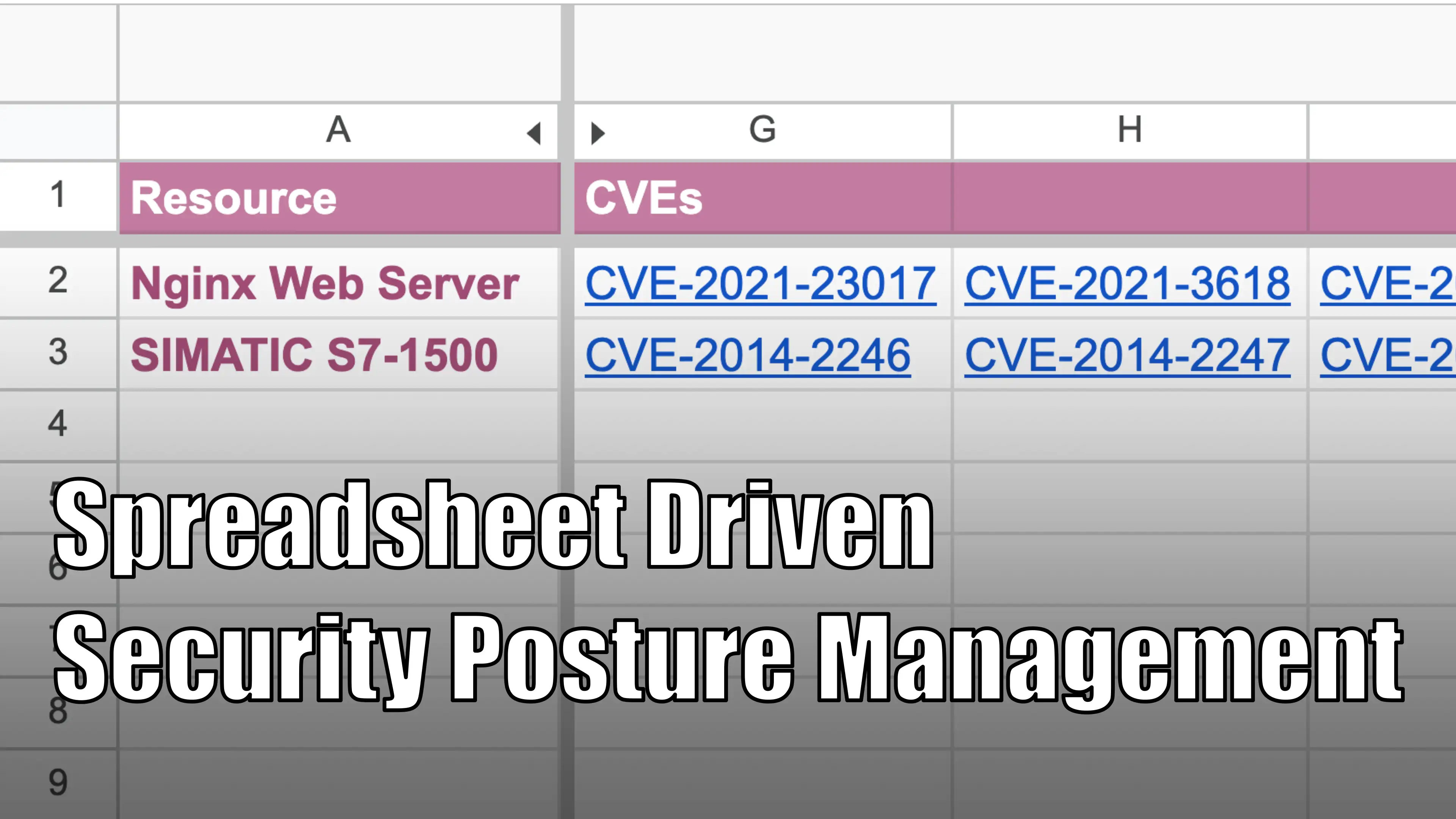
In this article, we’ll cover how to query the NIST vulnerability database, create a CPE Name for a resource, and automate the fetching of vulnerabilities with a script.
Let’s take the Apple goto fail vulnerability in 2016, a single duplicated line enabled man-in-the-middle attacks on SSL communications involving Apple devices:
These errors are common and silly, but still dangerous; moreover, as code gets more complex, and as more resources you have, the bigger your surface attack. That’s why it’s so important to install security updates.
Vulnerabilities are your backdoor and can provide access in many ways. Allowing attackers to disrupt your service, obtain information about your infrastructure (so they can exploit other vulnerabilities), and in the worst cases, execute code that ends on a remote control. Once they are in, attackers can move laterally to other resources, accessing or encrypting your business data, using your resources for crypto mining, or altering your production line ever so slightly so you don’t notice but enough so production fails.
Nowadays attacks tend to start as automated processes executed by botnets that look for vulnerable services and automatically hack them.