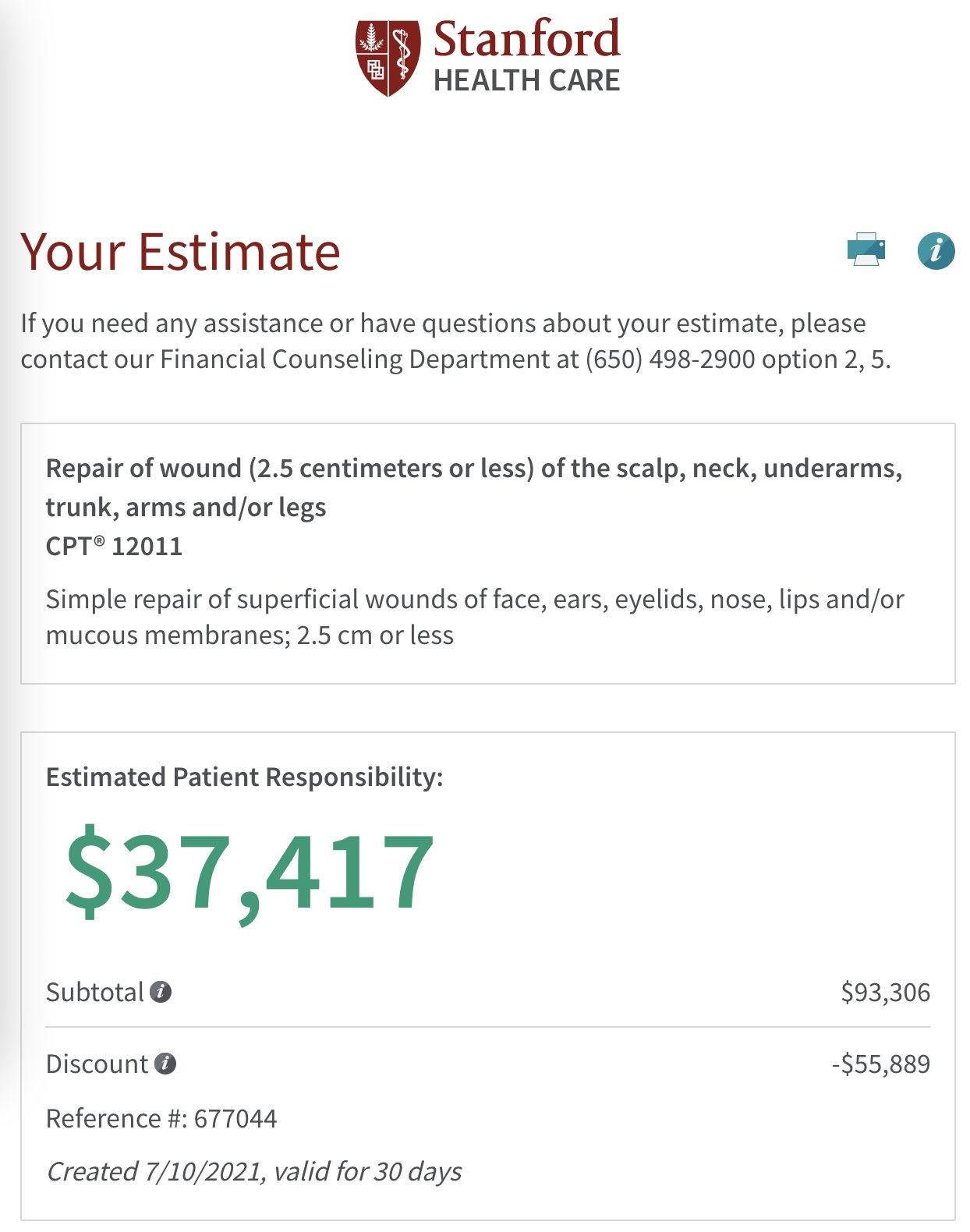
The 'Invisibility Cloak' - Slash-Proc Magic
While working my way through the excellent “Linux Attack, Detection and Live Forensics” course from Defensive Security, I read the following line: If you are looking for a simple way how to hide your process from the process list, then the bind mount operation is the answer. In order not to violate any copyright, I googled around and found the following gist from Timb-machine, where the same commands of the course are reflected:
I couldn’t find out who first developed this technique, but if somebody pointed me to a blog or paper with more information, I’d be happy to update the blog post.
The code or technique was not explained further in the course, only hinting that it can be used to hide processes from the process list. In the following blog post, we will take a closer look at how this technique works, whether we can hide our processes so easily, and more importantly, which forensic artifacts we can use to detect this technique.
To avoid recreating recreate the wheel, the following is a screenshot from an excellent answer on stackexchange to the question: “What is a bind mount?”.
Leave a Comment
Related Posts
Does/did anyone else have a hard time understanding classes and how to use them? : learnpython
Comment
Dmitrii on Twitter: "Let's talk about the Web, UIs and layout. I often hear: well, it's an amazing layout system. If there's anything lacking, show me anything that works under the same constraints: having to work with multiple screen sizes and adapt to them seamlessly. Well, a thread🧵 1/"
Comment
Jasper on Twitter: "got the Source Engine implementation running under latest WebGPU. these include some of the most complicated materials & shaders in noclip. it's exciting because it doesn't look any different!… https://t.co/wz27v8XfMm"
Comment