Parrot Anafi Drone Reverse Engineering
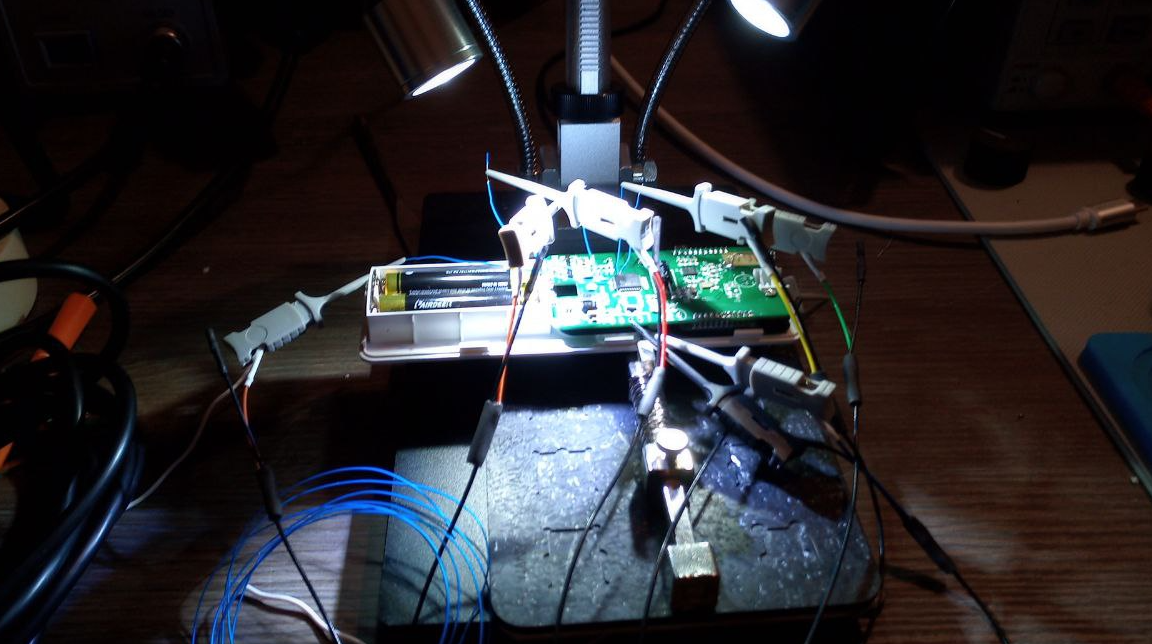
In this example, we demonstrate how we reverse-engineered the communication between the Parrot Anafi consumer drone and its controller, which connect via Wi-Fi. The Parrot Anafi hosts its own Wi-Fi network, allowing either the controller or a phone running the Freeflight app to connect. Our goal was to understand the signals sent to the Anafi for initiating takeoff and landing sequences.
Start by connecting your PC to the Parrot Anafi’s Wi-Fi network. Next, set up an ARP spoofing attack to place your PC in a man-in-the-middle position between the drone and its controller. This can be accomplished using tools like Ettercap, allowing your device to capture the data exchanged between the two.
Using Wireshark, we can look at the packets, which are send during a landing and a starting sequence (picture shows just a snippet):
We can see that the communication between the drone and the controller is done over UDP. Every UDP packet had some kind of hex string as payload, which was non-ASCII
Leave a Comment
Related Posts