Uncovering Apple Vulnerabilities: The diskarbitrationd and storagekitd Audit Story Part 1
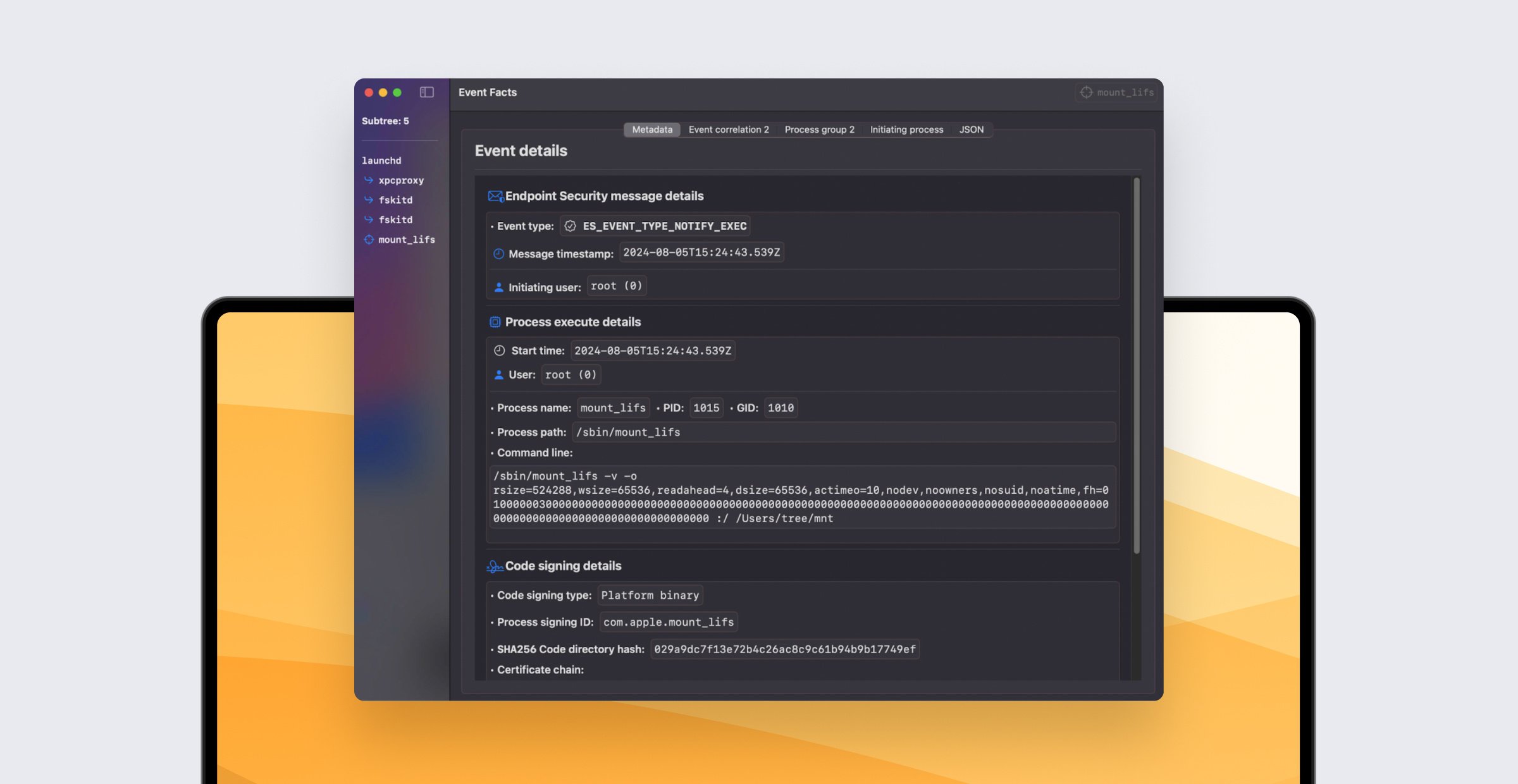
The Kandji team is always looking out for how to help keep your devices secure. In line with that, our Threat Research team performed an audit on the macOS diskarbitrationd and storagekitd system daemons, uncovering several vulnerabilities such as sandbox escapes, local privilege escalations, and TCC bypasses. Our team reported all of them to Apple through their responsible disclosure program, and as these are fixed now, we are releasing the details.
This is part one of a three part blog series, and in each part, we will review a vulnerability, how someone could exploit it, and finally, how Apple fixed it. We also presented these findings at the POC 2024 and Black Hat Europe 2024 IT Security conferences. With that context, let's dive in.
The diskarbitrationd process has been exploited multiple times in the past, and I already found numerous vulnerabilities in this daemon before. I covered those in my "History of macOS Disk Arbitration vulnerabilities" talk at the MacSysAdmin 2024 and Hacktivity 2024 conferences. Since then, I learned new tricks and techniques on macOS, and with this I thought that the daemon deserves a second look as there might be leftover issues.
Leave a Comment
Related Posts
Create a Scalable Real-time communication App like WhatsApp with Messaging, Video and Voice calls — Part I
Comment